What do you know about Ransomware?
This week we have learned of another version of Ransomware that has been found, this version called "Bad Rabbit" is in Europe now but could be here any day, or another version of it could jump over the ocean. It leads me to the question; what do you know about Ransomware? Not just the word that is in the news - do you know what it is, what it does, and how it happens? Worse yet what do you do when you do get it? I can speak in depth on this subject as having been through and attack like this before. It is an ugly situation which evolves so quickly that you have already lost all of your data before you know what happened or that it is even happening. By the time you figure out that it is going on you have most likely lost most of your business data. I was lucky and I had prepared for such an incident, I knew that no matter how much training users had or how much security I put in place that there is always a gap that something can come through. I had backups – this was the savior and I want it to be for you as well.
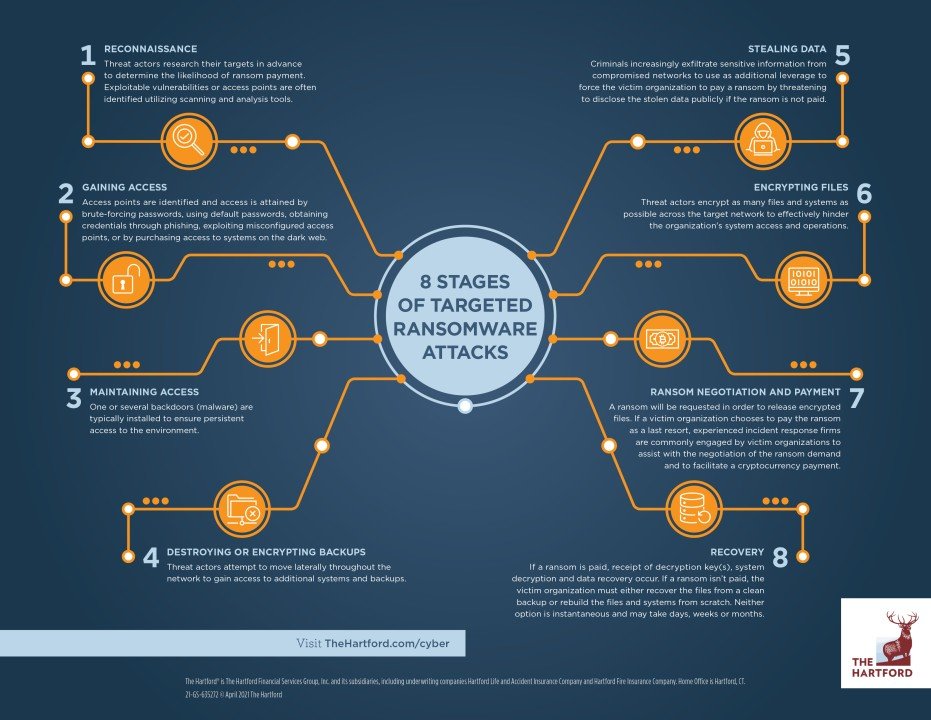
How it works:
Carbon Black has a nice writeup which outlines the steps quite clearly.
End user receives an email that appears to be from their boss, friend, family member, or another trusted person.
The email contains a URL to an application such as Salesforce, Workday or ZenDesk, etc...When you open the link it directs the user to a website which seems legitimate.
The page is actually a landing page for an exploit kit hosted in a .co.cc top level domain (TLD).Upon loading the page, the web server hosting the exploit kit begins communicating with the victim machine.
The server sends requests about versions of software such as Java of Flash to find a vulnerable version for which the kit has an exploit. And once it confirms the presence of the software it attempts to push an .EXE file to the computer which will attempt to execute on your local machine.Once execute, the program spawns child processes, including vssadmin.exe (shadow copy), to delete existing shadows on the victim machine and create new ones to hide in.
The attacker does this to limit the possible recovery of files by the victim using Shadow Copies that Windows stores on a system.The binary uses a PowerShell executable to propagate copies of itself throughout the filesystem.
The executable also searches the filesystem for files of specific extensions and begins to encrypt those files.The powershell.exe child process creates three copies of the originating malware binary, first in the AppData directory, next in the Start directory, and finally in the root C: directory. These copies are used in conjunction with the registry modifications to restart the malware upon reboot and login events.
After encrypting the victim’s files, the malware sends the encryption keyand other host- specific information back to the command-and-control server.
The server then sends a message to the victim.
This could be a simple “alert user of encryption and directions on paying us.” It could also include directions that result in downloading additional malware, which enables the attacker to steal credentials from the victim as well.
To amplify the victim’s distress, ransomware often includes a countdown clock with a deadline for paying the ransom – or else the decrypt key will be destroyed, eliminating any chance of recovery.
Paying the ransom often means the attacker will unlock the victim’s machine or provide the key to decrypt files. However, it rarely means the originating malicious binary, “ransomware.exe” in the case above, has been removed. That will require IT and SecOps support.
And the attack doesn’t necessarily end there. Attackers often load additional malware on a user’s machine, allowing them to harvest personal information, intellectual property, and credentials to sell for additional revenue.
So, what do you do next?
The answer to that question depends on your level of IT experience and planning that you have done before hand. You can pay the ransom, but this will most likely not result in decryption of the files. You could wipe your machine and start all over – this is not a satisfactory solution for a business or for your family files that you have had for years. If you have done proper preparations you can restore your servers or systems back to the state they were in right before the attack.
If you encounter this terrible situation Sparrowhawk can help you out, we specialize in affordable backup solutions for businesses, which can restore you back to a running state quickly. We can save your business data as quickly as you lost it. Whether you want us to handle the entire process or just work with your existing IT department we can get your business data safely backed up both at your location and if you choose securely off-site. We can meet compliance requirements for different institutions if needed as well.
Sparrowhawk – keeping your technology safe.